Homelab Update Dec 2024
As with all good I.T. people these days, I have a homelab. An environment within my home that allows to freely learn new skills without breaking anything in production. At least anything in production of my employer.
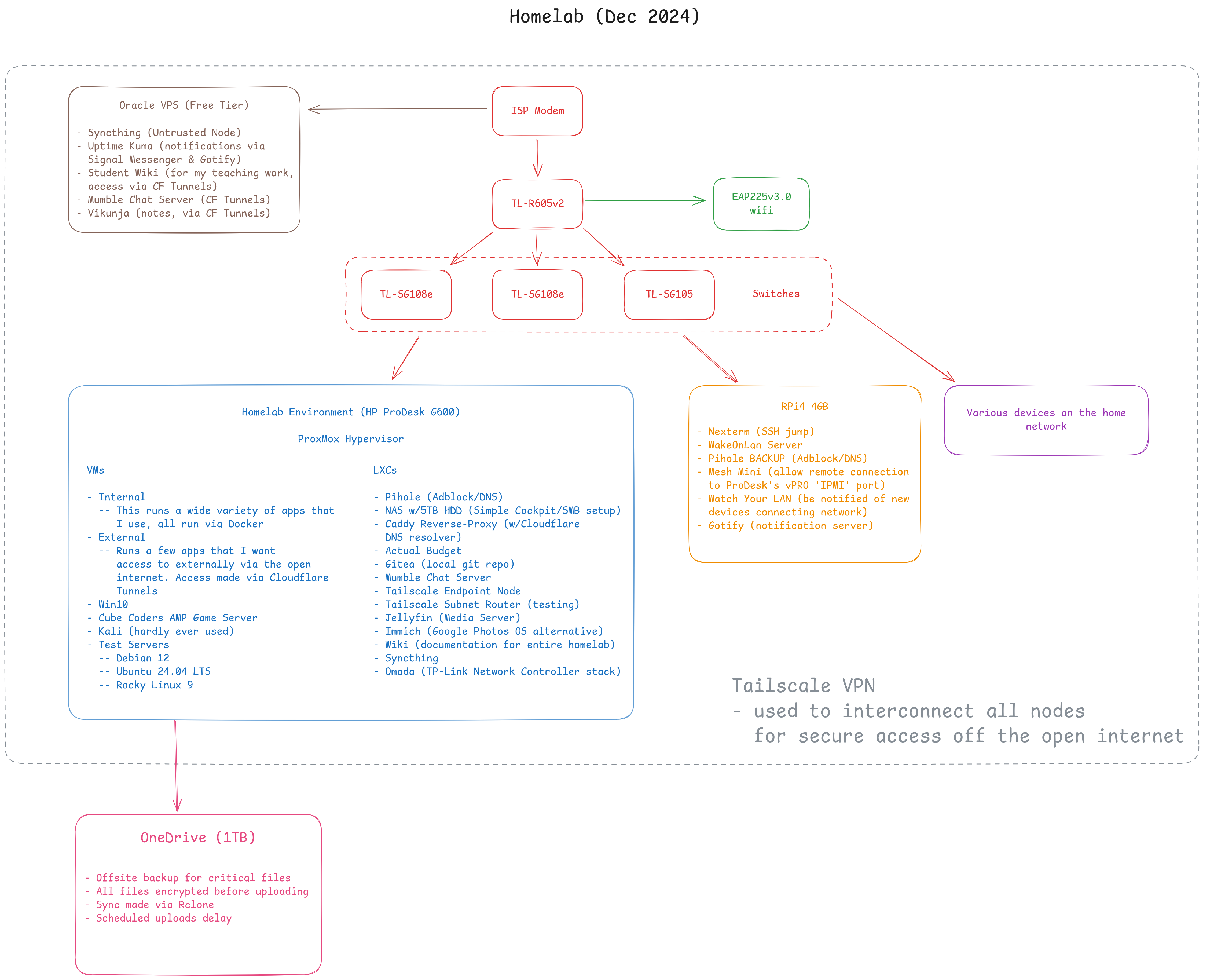
Below you will find the current layout plan, proving a bried overview of everything, and below that some descriptions of what is what.
Layout
Feel free to click the image to enlarge.
Network stack
Here I have decided to go with the TP-Link Omada lineup for the following reasons:
- TP Link is a known quantity with good product support, and the company shouldn’t be dying any time soon
- I get a similar experience to Ubiquity, but without the “Ubiquity tax”
- I can get a decent experience setting up complicated networks (when I eventually swap out my small switches for an Omada variant)
The purest in me says I should run OpnSense, however that would require further hardware outlay, and living in Brazil means that I have to pay outrageous taxes anytime I wish to enjoy new technology. That’s not happening right now.
Also the wife would balk at another “I need this for my job” purchase.
All things considered though, I’m very happy with this setup, and the Omada Software Controller works well in a Docker container.
Hardware
Proxmox host
I was very lucky to be gifted my HP ProDesk G600 (thanks David!!), and it has performed amazingly for my needs. Low power draw, and more than sufficient power output for my needs. The specs are as follows:
- CPU: Intel i5 10500T
- RAM: 32GB DDR4
- Storage:
-
- SSD1: 1TB NVMe (boot, Proxmox, VM storage)
-
- SSD2: 2TB NVMe (bulk storage for Immich photo backup)
-
- HHD1: 5TB HDD via USB (for NAS duties)
-
- HHD2: 500GB (currently unused)
- Networking:
-
- NIC1: 1Gbit (built-in)
-
- NIC2: 1Gbit (USB-C, soon to be used to create isolated test network)
Raspberry Pi4 4GB
This device is the fallback. I use the RPi as my SSH jump host via an amazing app called [Nexterm}(https://github.com/gnmyt/Nexterm), so I always have a common access point. Access via a browser is a nice bonus.
Additionally, the core use case of the RPi is a WakeOnLAN server, so should the main homelab go down, it gets pinged every 2min with a Magic Packet to bring it back online. Very cool stuff!
The Pi also acts as a secondary host for UptimeKuma and Gotify so I can keep abreast of the happenings on my homelab (such as the completion of backup scripts and VM backups etc.)
Finally, I run Mesh Mini which allows me to tap into the Intel vPro “IPMI” functionality, allowing me to manipulate the device over the network, even if it is shut off. Due to the VPN setup to my Pi, I can access this even remotely.
Oracle Cloud VPS
I have this VPS running on Oracle’s Free Tier. This, according to the Homelab subreddit, is playing with fire potentially as Oracle is known to just randomly shutdown free tier VPS’s without prior notice or reason. As valuable as this VPS is to me, I do run automated daily backups down to my NAS. So heaven forbid this were to just shutdown one day, it wouldn’t be the end of the world.
This VPS is predominantly used for monitoring my home network and sending notifications to my phone should any service go down. This is handled by Uptime Kuma and Gotify It also hosts a wiki for my English students (my other job) to aid my teaching. This is hosted on an instance of Material for MkDocs, as is my own Homelab wiki for that matter.
App stack
I won’t bore you with all the apps that I run and why, but rather how they hosted.
Docker containers are my hosting method of choice since they provide the secuirty and flexibility that I need. I generally prefer to use bind mounts as opposed to volumes as they are easier to store and backup.
As much as it’s onmy list of things to learn, you won’t find any HA or Kubernetes setups here. For one, I don’t need the complexity, and second, since I only have one physical host, the setup won’t be truly HA. However, I will eventually tinker with this.
Access to my network and services is via my secure Tailscale Tailnet (more on that later). Whenever a service is requested via jellyfin.example.com (for example), Cloudflare receives that DNS request and redirects to my Caddy reverse-proxy. When I’m on my internal network, DNS resolution is handled by Pihole, and the redirect is made one again to the Caddy reverse-proxy.
Security
This is one area where I really need to apply some focus. Currently, the security is adequate for my setup. The majority of services are not on the open internet, and those that are are isolated. However, soon I will begin studying the CompTIA Security+ course and I’m sure the learnings from that will help me in this area immensely.
VPN: Tailscale Tailnet
This is my primary mode of access to my homelab, even locally. I use the Tailnet IPs when SSHing just out of habit since I will then always use the same stuff. Less to have to remember that way. Actually, Tailscale has it’s own internal “MagicDNS” which allows me to use the device hostname, so that makes things eaiser still.
There’s not a whole lot to explain here, their website does a pretty good job of it. But basically, install the app on the host/client, sign in with SSO (Google, Microsoft or Github), connect the device to the Tailnet and off you go.
So, that’s it really in a nutshell. The homelab is ever evolving and providing new avenues for learning and frustration, but I love it!